F(Ph)ishing in Cyberspace?
Abhishek Sinha[1],
Sahana Shenoy1 and Lalitha Sreenath[2]
Published in TAPMI Compendium 2006
With the
increased use of the Internet as a convenient vehicle for communication – be it
personal or professional, the scope for cyber criminals to prowl around for
sensitive information by committing security breaches has correspondingly
increased. This paper attempts to focus on the growing menace of theft of vital
information from the netizens in cyberspace, euphemistically described as
“phishing”. Despite all attempts to counter such occurrences through more and
more sophisticated technological innovations, the scourge cannot be contained
efficiently by technology alone. Hence, this paper is an attempt to create
awareness about the various methods of phishing that have been documented until
now and the various precautionary measures to avoid exposure to such criminal
activities.
INTRODUCTION
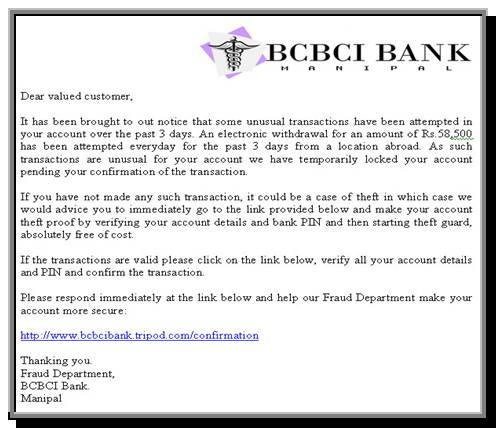
If you have an account with BCBCI Bank, what would you
do on seeing a mail like the above one? Would you panic, click on the link go
to the website provided and submit your account number, PIN and address for
verification and to stop the supposedly fraudulent transaction? Most people
would. And the result could mean a loss in thousands, and sometimes lakhs of
rupees.
This innovative form of cyber crime is fast becoming
endemic and is causing widespread damage ranging from simple loss of e-mail
id’s to financial losses amounting to crores of rupees and millions of dollars.
In a world where technology penetrates deep into every individual’s life, the
bait can be directed at anybody and everybody: - a stock broker, an engineer, a
professor or just a student, - all are potential targets for all phishers in
the web world. The only weapon against such fraud is the awareness of this
concept and the technology that could leave anyone gasping like a fish out of
water!
(Note:
The above mail is fictitious and for educative purposes only)
HOW
IS IT DONE?
The principle behind the concept of Phishing is simple
impersonation or identity theft. The perpetrator or phisher simply pretends to be
a person, organization or entity whom any person would trust, like one’s bank,
lawyer, e-mail service provider, credit
card company, employer, or even Network Administrator. To mislead gullible
persons to believe in the authenticity of the message that is sent, the phisher
usually adopts several methods: a spoof website which is absolutely identical
to the website of the original e-mail service provider, an instant message from
an ID which seems to be that of the Network Administrator, or simply an e-mail
with the bank logo, which assures the reliability of its origin from the bank.
Once the receiver of the e-mail gets convinced that it is a communication from
a trust-worthy entity, the victim has bitten the bait, and he now feels obliged
to submit crucial and confidential information regarding his bank account,
internet service, e-mail account, or his organization details. Once such
crucial information is communicated, it goes directly to the phisher, who can
use this information to transfer money from the victim’s account, make
purchases with the credit card, hack into the victim’s website, or simply
gather confidential information regarding his organization. In short the victim
voluntarily hands the keys of his vault to the phisher who can then use keys to
do whatever he may desire!
Through E-mail
Phishing is done with the help of some simple software
and social engineering, both of which are used to bluff the unsuspecting phish
(Callaghan, 2005). It is possible for the
phisher to imitate the bank or the organizations mail, complete with logo and
the formal language which organizations use in official mails and to send a
simple disguised mail to customers. A good example is the above mail. The mail
might simply ask recipients to reply at a given address which would in effect
amount to asking the victim to mail back the required confidential information.
As phishers use creativity in trying to disguise their mail ids to look genuine
ones, the only clue to counter the Phishing through mails is to check the mail
id itself carefully.
For instance, take the example of an id - senior_technician@dellmail.com.
This seemingly official e-mail ID can pretend to belong to a Dell home-repair
technician and might ask a computer owner to disclose his/her account details,
address and even timings when the person is and is not at home. Such
information might then be used to steal money, make illegal financial
transactions or even organize a theft from the concerned person’s house once
his/her timings are known. This whole operation however needs absolutely no
hacking tools. “Dellmail” is a free e-mail service provided by the Dell  Company and an ID “senior_technician” would be easy to
create. Hence the mail id senior_technician@dellmail.com
is easily obtained. And the job thereafter is just to copy and paste the target
organizations logo and send the mail.
Company and an ID “senior_technician” would be easy to
create. Hence the mail id senior_technician@dellmail.com
is easily obtained. And the job thereafter is just to copy and paste the target
organizations logo and send the mail.
Through
Website
Some
phishers use impersonated websites to spoof the phish into disclosing
information to capitalize on the cautious nature of some customers who would be
wary to part with personal information over the mail be but very glad to submit
information on specified input fields on a website. This type of Phishing also
has been shown to be successful, as generally not all of the netizens are aware
of specific domain names owned by organizations. (Dan Jones, 2005)The website referred to in fig. 1 is http://www.bcbcibank.tripod.com.
“Tripod” is a service provider which provides domain space and web hosting
services free of cost. This would mean that a phisher can actually make a
website with the above URL absolutely free of cost, and then proceed to dupe one
and all. It is interesting to note that BCBCI Bank, if such a bank existed,
would always have a website hosted on its own server and would hence have a URL
like http://www.bcbcibank.com which
clearly indicates that it is not a website hosted on a free service provider’s
server. However sometimes it is easy to fool a target phish by registering and
using a similar sounding domain name like http://www.bcbcibnk.com
(Note the spelling discrepancy). However this is a slightly expensive technique
as the phisher would actually have to go and register such a site. Another
method would be to simply embed a hyperlink in the content text of a webpage
(for e.g. “Please click HERE
to confirm your account details”). There are other methods like spoofing
the address bar in your browser so that it actually shows that you are on the
authentic site, though these fraudulent practices can also be easily
identified.
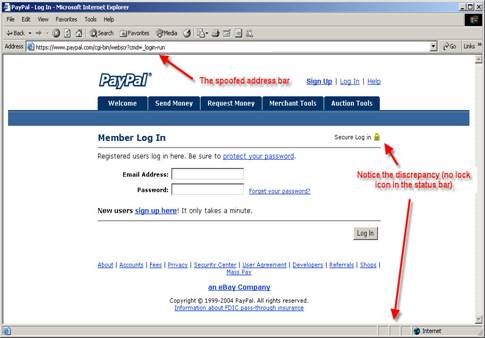
PayPal has been one of the biggest and most prominent
targets of Phishers and cases of PayPal Phishing can today be found in many
hacking historical archives. Given below is a spoof website of PayPal which
asked users to login (thus obtaining their password) and then asked them to
submit and verify account information. (Source: http://www.antiphishing.org/)
Note the discrepancies marked by the arrows.
As
the arrow highlights, the above site uses a spoof address bar, which could be
one superimposed on the original address bar on the browser. Also there is no
padlock icon in the status bar. However if one were to right click on the
website and go to properties he would be seeing the properties window as seen
in the attached screen shot. The ellipse highlights the actual URL of the spoof
site.
Hence
with a few clicks of the mouse and checking the properties, padlock item etc.
of a website before submitting any personal or confidential information, loss
of thousands and lakhs of rupees can be averted! More information about
avoiding this kind of  Phishing is given in the section “Ways to Become Phish-immune” below.
Phishing is given in the section “Ways to Become Phish-immune” below.
Through Pop-up
Messages
Phishing
may also be in the form of a message which pops up while the target is using an
instant messaging service or while accessing a site which might be connected or
monitored by a spoof fisher website. The message might sound extremely
technical in nature in order to misguide the target to think it is a technical
failure. It also might hold a note of urgency in order to make the user submit
confidential information before he has time to think. In a research paper
published in 1998 by Gordon and Chess a typical message is described as below:
“Sector 4G9E of our data base has lost
all I/O functions. When your account logged onto our system, we were
temporarily able to verify it as a registered user. Approximately 94 seconds
ago, your verification was made void by loss of data in the Sector 4G9E. Now,
due to AOL verification protocol, it is mandatory for us to re-verify you.
Please click 'Respond' and re-state your password. Failure to comply will
result in immediate account deletion.”
PHISHING
IN INDIAN WATERS
Indians: The Target of Phishers
It
is high time that
Approximately 74% of the IT managers
from
A very interesting survey called ‘2005 India Web@work’ carried out by
Websense Inc. points out that an amazing 32% of the employees in India confessed
to having submitted extremely confidential information like credit card numbers
and corporate network passwords when targeted by Phishing attacks. The extent
of damage these incidents of fraud can cause is evident from the fact that a
huge 62% of these Indian IT managers said that a security breach in their
company and under their supervision would surely put their job at risk.
Interestingly, it has been noted in the survey, that most of the managers found
handling these security breaches more stressful than handling a minor car
accident!(“74% IT managers receive
phishing attacks” www.financialexpress.com)
In a very recent incident there have been reported
cases of Phishing with ICICI Bank as the target organization. In order to prevent
this ICICI Bank has issued a common e-mail to warn and inform all its customers
(using net-banking) of the threat they are all exposed to. The fact that
education and awareness of Phishing techniques can be effective in prevention
is confirmed by the action of ICICI Bank in this case. A sample of the mail is
given below.
|
|
|
|
The Instrument
of Phishers
Looking at it from the other perspective, Indian servers
are also becoming the hub of Phishing activities and a lot of phishers are
carrying out their fraudulent activities out of the Indian network environment.
Till now 23 organizations have
reported phishing attempts of their customers and users to the Government of
India. These include big finance players like Bank of America and J.P. Morgan
Chase. Government sources have revealed that the servers from which Phishing
attempts have been traced include prominent Indian names like Bharti, Sify,
Infotel, Net4india, Tata TeleServices and VSNL (Mayank Tewari, “Phishing by Indian servers”, ![]() Hindustan Times, New Delhi, December 7,
2005). Hackers follow the simple procedure of first hacking into the servers of
these Internet Service Providers, then creating spoof websites of target
organizations, and finally sending out bulk, or specific targeted e-mails to
their phishes to obtain classified information.
Hindustan Times, New Delhi, December 7,
2005). Hackers follow the simple procedure of first hacking into the servers of
these Internet Service Providers, then creating spoof websites of target
organizations, and finally sending out bulk, or specific targeted e-mails to
their phishes to obtain classified information.
The Computer Emergency
Response Team (CERT) has been established to tackle this international
problem. However, it has been opined that CERT, may not be effective as it is
not endowed with any investigative or penalizing powers. Better government
initiatives coupled with creation of awareness amongst all netizens are prime
requisites to make the subcontinent on the
However considering that most Indian servers today are
becoming targets for phishers who need a base and location to carry out their
Phishing activities, it has become necessary for business organizations to
spruce up the network security and install a number of barriers to protect the
network from hackers, spammers and phishers. Generally, administrative rights
are not given to all users of the LAN in the organizations. This means that
installation of any software is not allowed from general user nodes and
requires special administrative rights. This prevents the installation of any
viral software and also eliminates the chances of static viruses or Phishing
software from residing and operating from the organizations’ network. For
instance, TAPMI has a dual firewall to keep out intruders. At the first level
TAPMI has Zywall, a hardware firewall
and at the second level it has ISA 2004, a
Microsoft firewall which is a part of the server package[3].
WAYS
TO BECOME PHISH-IMMUNE:
- Crucial information
should never be sent in an e-mail. Bank or credit card companies will never
ask information like credit card number, bank account PIN or other
confidential information to be sent in an e-mail. Hence, on receipt of any
e-mail asking for verification or reconfirmation information or an e-mail
informing of any discrepancies in the bank account, it is always advisable
to get in touch with the bank personally (via phone or personal visit).
The bottom line is to avoid sending confidential information online as far
as possible.
- It is also necessary
to know the exact domain names or URLs of the bank, credit card company,
e-mail service provider and other service providers with which one
regularly deals. For instance, if the bank is BCBCI Bank, it should be
noted that the bank’s URL could be http://www.bcbcibank.com
or http://bcbcibank.com; it would be
highly improbable that the URL is http://www.bcbcibank.tripod.com.
An institution as important as a bank will usually pay for a unique domain
name and host its site on a personal secure server. Hence it would not
have an alien extension like “Tripod” in its domain name. These extensions
come when websites are hosted on the servers of free websites-hosting service
providers like Tripod, Freeservers etc. Hence before providing any kind of
information on any website, it is advisable to look at the address or URL
bar of the browser. This simple exercise alone could save a lot of
trouble!
- Sometimes the phishers
are clever enough to disguise the URL address so that it appears as a
valid one in the web browser. In such a case the only way to check the
authenticity of the website would be to right click with the mouse on any
part of the website display in the browser and in the menu when
“properties” is clicked, it will always display the correct URL.
- Another way to make
sure that the website being currently accessed or viewed is a secure one,
and has not been spoofed or manipulated by phishers is to check the bar at
the bottom of the browser for a small padlock icon. This padlock icon
depicts that the accessed website is a secure one; to get more information
about it, one can click on the padlock, and the security certificate of
the website will be displayed.
- Since, apart from
financial and bank details, phishing is also done to obtain corporate and
company sensitive data, sending of company or organization sensitive
information to external e-mail ids should be totally avoided. If the name
of an employee is “abc” working for a company named “xyz” and the office
e-mail id is abc@xyz.com then, the network
administrator would have an id similar to administrator@xyz.com.
Hence any e-mail from administrator_xyz@yahoo.com
claiming to be the network administrator of xyz company and asking for
confidential information or the reconfirmation of password, could be a
“phishy” situation.
6.  It is also advisable to have an up-to-date version of
the browser which is used to browse the internet. Software providers keep
updating their browsers to eliminate all kinds of security breaches and correct
all gaps and shortcomings in the security measures in the coding of their
product. For Internet Explorer, a special patch which counters certain phishing
schemes can be downloaded from http://www.microsoft.com/security/. Microsoft also provides a Phishing
Filter Add-in which according to the Microsoft website “provides dynamic protection against Phishing
scams as you visit Web sites in two ways….
It scans and helps identify suspicious Web sites, and provides
up-to-the-hour updates and reporting on known Phishing sites.”
It is also advisable to have an up-to-date version of
the browser which is used to browse the internet. Software providers keep
updating their browsers to eliminate all kinds of security breaches and correct
all gaps and shortcomings in the security measures in the coding of their
product. For Internet Explorer, a special patch which counters certain phishing
schemes can be downloaded from http://www.microsoft.com/security/. Microsoft also provides a Phishing
Filter Add-in which according to the Microsoft website “provides dynamic protection against Phishing
scams as you visit Web sites in two ways….
It scans and helps identify suspicious Web sites, and provides
up-to-the-hour updates and reporting on known Phishing sites.”
![]()
This Add-in is free and is available for MSN Search
Toolbar, and Microsoft claims that it will also be available in the upcoming
Internet Explorer 7.
This add in gives you warnings as and when you visit
suspicious websites and automatically blocks a website which is known for sure
to be a spoofed Phishing site. This add-in can be obtained from the Microsoft
main site.
![]()
Similarly every software provider will have updates
and patches for their respective browsers. Apart from these there are special browser
extensions which can assist you in detecting a spoofed website. An example of
such software is SpoofStick and more of such anti-spoof software can be found
in the following websites: (http://www.corestreet.com/spoofstick/,
http://www.pcworld.com/downloads/file_description/0,fid,23319,00.asp)
SUGGESTIONS
India as the emerging IT and ITES hub of the world has
to take cognizance of cyber security issues - phishing, cracking, etc. which
may affect India’s position in the IT industry. If
Many suggestions have been made for effectively
addressing IT security concerns like Phishing (www.antiphishing.org). One[4]
such relates to the establishment of a NGO consisting of volunteers - ideally
those in the IT community, ranging from IT Security Consultants, Industry
Analysts, IT Governance Experts and even students with a technical or
management background to act as a strong advisory force for tackling cyber
discrepancies. Such an organization would not only help fight the menace of
cyber crime ourselves but also help the regulatory bodies frame legislations
and policies to make our country an “IT Safe Zone”[5].!
Even as our nation grows in terms of GPD, it also
develops as a target for fraudsters. The increase in financial power of the
individual should also be supplemented by an increased awareness of the ways in
which he can be cheated. Despite installation of numerous anti-virus and
anti-hacking software and multiple firewalls in our network environment, the
most effective weapon against Phishing (or any kind of e-fraud) will always be
information and knowledge. As we plunge into the Information Age at a million
terahertz speed, we need to realize that this Age is not just about Information
Technology, but also a lot about Information Awareness (www.rediff.com).
REFERENCES
Callaghan, H. 2005. Phishing – don’t get reeled
in! http:// www.tecbrand.com/
eyrisk/newsletter0405/april/hackers_phishing.html.
Gordon, S. & Chess, D. M.
1998. Where there's
smoke, there's mirrors: The truth about Trojan horses on the internet,
presented at the Virus Bulletin Conference in
http://www.antiphishing.org.
http://www.financialexpress.com/fe_full_story.php?content_id=98848.Financial Express, 2005.74% IT managers receive phishing attacks.
http://www.microsoft.com/athome/security/email/phishing.mspx.
Microsoft, 2005. Help prevent identity theft from phishing scams: What is
a phishing scam?
Jones,
D. 2005. Phishing for your identity. http://www.colorado.edu/its/security/
awareness/apr05phishing/phishingidentities.html.
Survey 2005
Tewari, M. 2005. Phishing by Indian servers. http://www.hindustantimes.com/
news/181_1567900,0035.htm.
BIBLIOGRAPHY
Rediff, 2004. What's
phishing? How to be safe?
http://inhome.rediff.com/money/2004/dec/20spec.htm.
The Honeynet Project and
Research
IMAGES
http://www.dellmail.com/scripts/common/index.main?signin=1&lang=us
http://www.microsoft.com/athome/security/email/phishing.mspx
http://www.antiphishing.org/
